select
Information Communication Security Management
Information Communication Security Risk Management Framework

Implementation results of the promotion of enterprise information security measures.
Information Security Risks and Countermeasures

In order to strengthen information security protection and identify information security risks, countermeasures are proposed and the results are regularly reviewed.
Major Information Security Incidents

So far, there has been no major information security incident causing business damage.
Date of Submission to the Board of Directors

2024.11.11.
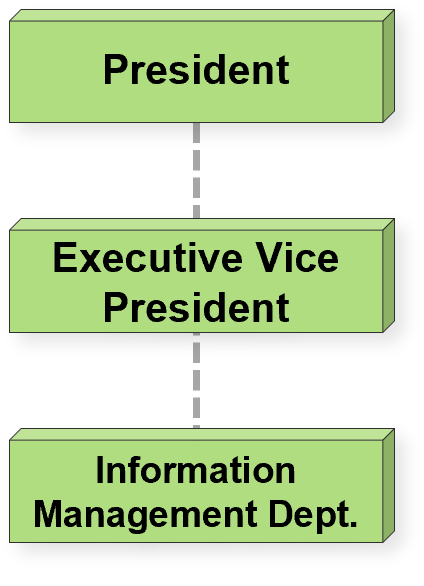
In order to implement the Information Communication security strategy set by the Enterprise Information Communication Security Organization, and ensure the relevant standards, procedures and regulations of information security are followed. The President serves as the top manager of the organization, the Executive Vice President serves as the management representative, and the Information Management Department is responsible for coordinating and implementing the Information Communication security policy, publicizing the Information Communication security information, enhancing employees' information security awareness, and collecting and improving the technology, products or procedures for the performance and effectiveness of the organization's information security management system. The Audit Office conducts an annual security audit of the internal control system, evaluates the effectiveness of the internal control of the Company's information and communications operations, and reports to the board of directors on a regular basis every year.

Information Communication Security Policy

- Enterprise Information Security Management Strategy
-
Maintain the sustainable operation of each information communication system.
-
Maintain physical environment security.
-
Prevent hackers and various viruses from invasion and destruction.
-
Prevent leakage of sensitive information.
-
Prevent improper intentions and illegal use.
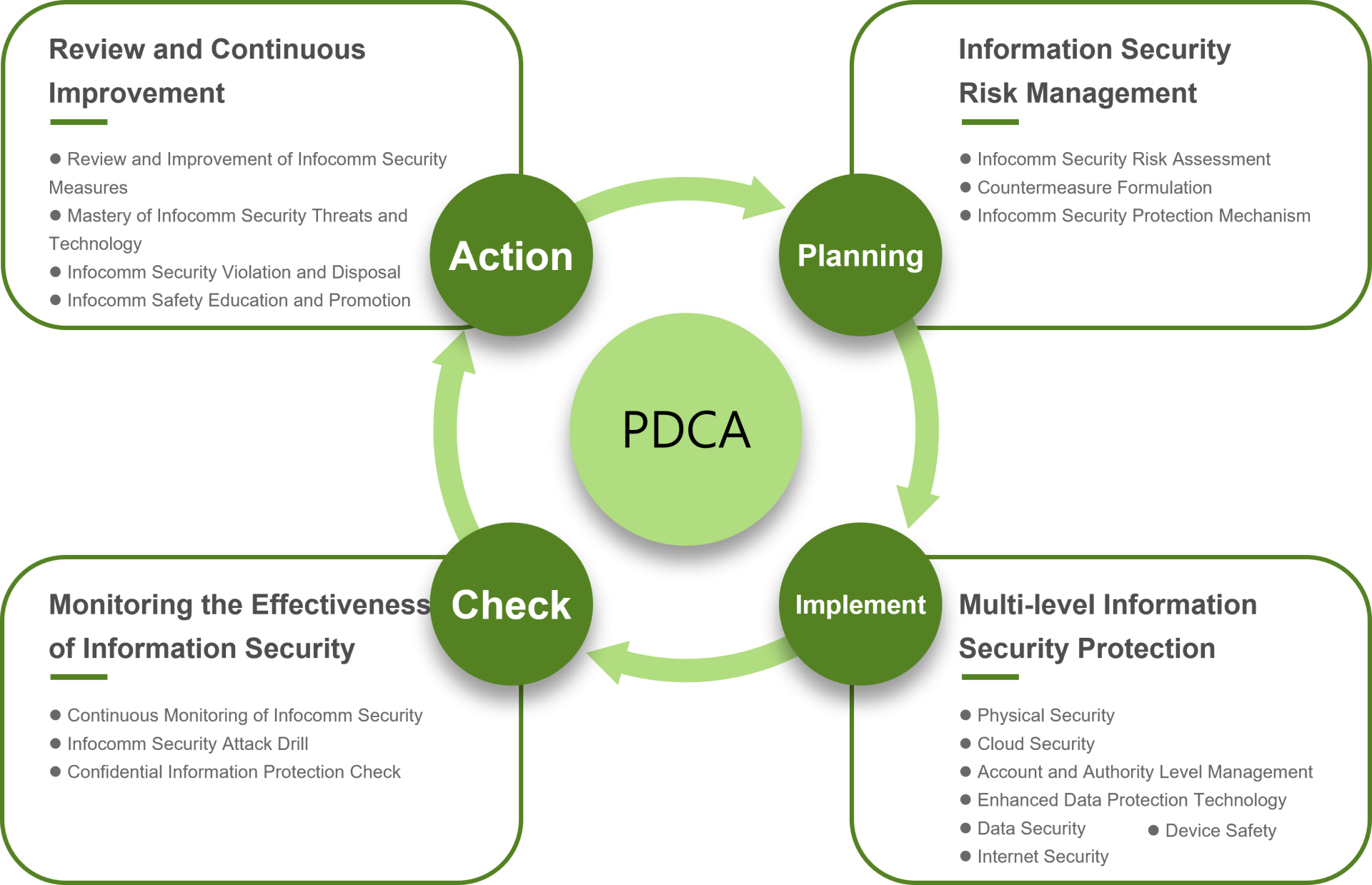
- Enterprise Information Communication Security Risk Management and Continuous Improvement Framework
PDCA (Plan-Do-Check-Act) cycle management is adopted to ensure goal achievement and continuous improvement.

- Specific Management Plans
| ITEM | SPECIFIC MANAGEMENT MEASURES |
| Physical Security |
|
| Device Safety |
|
| Internet Security |
|
| Cloud Protection |
|
| Data Security |
|
| Education and Advocacy |
|
- Resources Put in Information Communication Safety Management
Implementation results of the promotion of enterprise information security measures.
| POLICIES |
|
| TRAINING AND ADVOCACY |
|
| SYSTEMS |
|
In order to strengthen information security protection and identify information security risks, countermeasures are proposed and the results are regularly reviewed.
| SECURITY RISK IDENTIFICATION | IMPACT ASSESSMENT | COUNTERMEASURES | PERFORMANCE MANAGEMENT |
| Personal Computer Account Password Security | Financial business secrets are stolen by people with intentions. | The personal computer power-on password is changed regularly. | The password needs to be changed regularly and in accordance with the principle of complexity. |
| Computer Virus Protection | Computer viruses, ransomware, Trojans and mining programs. | Strengthen endpoint protection, and import behavior monitoring and application control protection system. | Strengthen system and data security by endpoint type. |
| Network Management Security | Network stability, deliberate attacks and traffic isolation. | Regularly update the firmware and import the Intrusion Prevention System (IPS). | When abnormal network packets or behaviors are found, the system will send an alert notification and take necessary measures immediately. |
| Information Security | Unauthorized access to information systems. | Establish an application authorization process according to job requirements. | The electronic form is used for application, and the access will be allowed after the approval of the supervisor and the responsible unit. |
| Online Safety | Malware, phishing, command and control of servers by zombie computers and other improper transmissions. | Import an advanced threat protection system, and conduct regular email social engineering drills every year. | Actively block zero-time-difference vulnerability attacks and warn of inappropriate transmissions. |
| Information System Service Operation | Hackers may try to infiltrate the Company's network systems with computer viruses, destructive software or ransomware in order to interfere with the Company's operations. | Set the Recovery Time Objective (RTO) and Recovery Point Objective (RPO) for the core business. | Set up an appropriate backup mechanism and backup plan, and regularly test the correctness of the restored data. |
Major Information Security Incidents
So far, there has been no major information security incident causing business damage.
Date of Submission to the Board of Directors
2024.11.11.

If you have any questions about sustainable operation, please contact us.
IR

E-mail : IR@anpec.com.tw
Tel : +886-3-564-2000
Address : No.6, Duxing 1st Rd., Hsinchu City 300096, Taiwan (R.O.C.)
Office hour : 8:30 AM ~ 5:30 PM
Securities Agent

MasterLink Securities Corporation (Securities Agent)
Tel : +886-2-2768-6668
Fax : +886-2-2768-8778
Address : B1, No. 35, Ln. 11, Guangfu N. Rd., Songshan Dist., Taipei City
Office hour : 8:30 AM ~ 4:30 PM
Website: http://www.masterlink.com.tw/
IR
E-mail : IR@anpec.com.tw
Tel : +886-3-564-2000
Address : No.6, Duxing 1st Rd., Hsinchu City 300096, Taiwan (R.O.C.)
Office hour : 8:30 AM ~ 5:30 PM
Securities Agent
MasterLink Securities Corporation (Securities Agent)
Tel : +886-2-2768-6668
Fax : +886-2-2768-8778
Address : B1, No. 35, Ln. 11, Guangfu N. Rd., Songshan Dist., Taipei City
Office hour : 8:30 AM ~ 4:30 PM
Website: http://www.masterlink.com.tw/


